In the past few years, there has been a worldwide rise in cyber attacks on Industrial Control Systems (ICS), and experts have been warning utility executives around the world about the potential threats. Two examples of threats include the recent string of Russian cyber attacks targeting U.S. Government entities and multiple U.S. critical infrastructure sectors, including the energy, nuclear, commercial facilities, water, aviation and critical manufacturing sectors1, and the 2015 cyber attacks on the supervisory control and data acquisition (SCADA)’s distribution management systems of three regional electricity distribution companies in Ukraine resulting in several power outages across various areas2. This article addresses the greater issue at hand – the potential future of these attacks, and whether this has become the new warfare. Attacks such as these have led to an intensified concern in various industries surrounding the protection of operational technology (OT) environments.
IT Versus OT
In a typical enterprise environment, protection of critical data is often seen as a top priority. This need is met by employing multiple Information Technology (IT)/ IS personnel to protect and combat potential cyber security issues. However, the common practice of protection of critical data is often not translated over to establishing the security of Operational Technology (OT) environments. What is Operational Technology? It is software or hardware that controls processes, physical devices and events in an enterprise, and ultimately alters the state of a system; such system can include access control, process control, surveillance voice technologies, etc. OT is categorically used interchangeably as a part of or as an Industrial Control System.
In mission-critical infrastructures, ICS such as power grids, mass transit transportation systems (e.g., airports, bus terminals, roadways or train stations), wastewater facilities and nuclear power plants, the emphasis should be not only on security for the IT assets but also on the often-overlooked OT assets. Let’s take, for example, a power utility company which has implemented enterprise systems and has its IT department devoted to protecting these systems. On the flipside, the company has field assets – transmission and distribution stations – which generate and distribute power to the consumers, and these assets are essentially the main driver of the revenue stream and the lifeblood for that company.
Having spoken with many customers, some are surprisingly unaware of the threats faced by their OT systems, and such companies often believe that closed systems not connected to the public WAN are safe from threats. In reality, this is simply not the case; those systems are highly vulnerable and being exposed to a cyber-attack after functioning long term without the capabilities of early detection or containment, they can suffer detrimental and crippling consequences in the aftermath of a cyber-attack.
Tactics and Techniques for Attacking OT Systems
For example, in the cyber attack of Ukraine’s power grid, the attackers’ tactics and techniques included:
- Spear phishing for gaining access to the business networks of the companies
- Different variants of the BlackEnergy 3 malware and manipulation of Microsoft Office documents that contained the malware to gain a foothold into the Information Technology (IT) networks of the electricity companies
- Theft of credentials from the business networks
- Use of virtual private networks (VPNs) to enter the ICS network
- Use of existing remote access tools within the environment or issuing commands directly from a remote station similar to an operator Human Machine Interface (HMI)
- Serial-to-ethernet communications devices impacted at a firmware level
- Use of a modified KillDisk to erase the master boot record of impacted organization systems as well as the targeted deletion of some logs
- Utilizing UPS systems to impact connected load with a scheduled service outage
- Telephone denial-of-service attack on the call centers the Human Machine Interface (HMI)2
Air Gaps Between IT and OT Networks
Historically and still in the present day, OT networks are legacy systems that were primarily isolated specialized systems using proprietary hardware and software. As such, they were not connected to the company’s enterprise networks and run independently, thus resulting in “air gaps” between the IT network and the OT network. Air gaps occur when one network such as IT has security measures that segment the IT environment from their unsecured OT counterpart. The good news is that with the advancements in technology, OT networks are moving towards a more converged network environment and more efficient control of data transportation, storage, data analytics and monitoring processes. However, now as a part of the converged network environment, OT network users and administrators must put serious consideration into the cyber threat landscape. Even governments recognize the need for cyber protection and have legislated Critical Infrastructure Projects (CIP) to implement threat measures for protection of critical systems. For this article, let’s focus on the OT environments and how to improve the resilience to cyber attacks.
Why Cyber Resilience is so Crucial
When it comes to cyber resilience, the rise of cyber threats against ICS globally should always be on the top of the CEO’s “to-do” list. OT networks have a different set of protocols from an IT environment. Availability or access to assets of a nuclear plant or power substation is a top priority for an OT network, versus an IT approach that prioritizes confidentiality as the number one concern. OT environments must have constant communications between devices monitoring or controlling critical functions. For example, critical assets in a nuclear plant that monitor thermal sensors could potentially prevent overheating and causing an explosion. Blocking of any virtual traffic due to security requirements to these critical assets may have severe consequences for the OT environment.
Simply put, blocking traffic in the IT world (e.g., in a bank) may cause the bank to lose some transactions. As a result, the bank can shut down that part of the system for containment and quarantine, but this will be by no means life-threatening. However, in the OT environment, blocking traffic can potentially lead to the death of an employee or others if the non-communicating device is responsible for process control and monitoring of a critical function such as cooling of a reactor at a nuclear plant. Even with accessibility as a top priority for OT networks, we can’t conclude that OT networks should not be protected or can’t be protected from cyber threats. Adversely, it is these types of systems that should be highly secure since they provide service with significant and immediate impacts on human lives that extend beyond the company’s human resources.
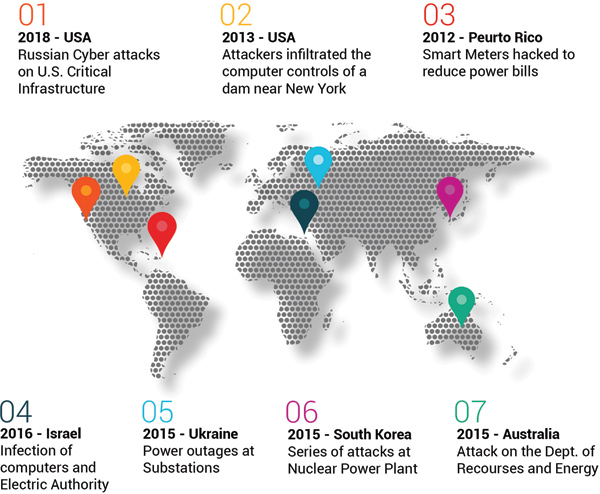
Examples of Significant Cyber Attacks in Industrial Control Systems
Hackers in Mission Critical Systems
Ongoing activities of hackers continue to threaten mission-critical systems as they see vulnerabilities in industrial networks worldwide. Once hackers have infiltrated your corporate environment, they can traverse through other unsecured networks within the OT environments, target vulnerabilities, and propagate within the company. These types of threats have essentially become the new warfare in the present world whether by solitary hackers or state-sponsored. (See map with scenarios of cyber attacks on ICS applications and their onward trends.)
Defense in Depth – People, Processes & Technology
When considering protecting your data, you need to look at a “Defense in Depth” multi-tiered or layered approach. There is no “out of the box security” that can provide a singular solution to stop cyber threats in today’s world. Security is not an isolated process but an ongoing process; hence, why a layered approach is needed to constantly protect your critical data. Using best practices, an organization could limit future attacks, essentially creating an ecosystem to ensure Cyber Immunity with a holistic view. It is the sum of all parts working together to ensure optimum performance. Technology alone, while playing a vital part, will not prevent cyber threats in today’s modern world. Rather, the principals surrounding Cyber Immunity should be developed and balanced around the fundamental pillars – People, Processes & Technology. Security for your organization should always be transformational to keep up with the latest threats and adjust to those threats within the pillars.
- People within the organization need to be made aware of the sensitivity of data; therefore, training staff about the potential threats and how to secure the data is essential. To ensure competency and mitigate risks, staff’s knowledge or skills should always be updated to reflect the latest technologies.
- Processes are important for the effective execution of organizational strategies. They define how the organization will react and follow a documented protocol for data protection.
- Technology is crucial for implementing controls for stopping and mitigating threats as well as logging and tracking user’s activities.
If we draw parallels to how the human body works, people also get viruses, and often relying solely on a body’s defense mechanisms and healing power may not be enough. A proper nutrition plan, along with adequate rest helps with the healing process, but at the end, a medication may be needed to start or bring to speed recovery. Generally, practicing good health, diet, exercise and proper rest daily could mitigate potential sickness down the road, improve immunity and make a person more resilient to sickness. In parallel, this holistic approach to wellness and health is not different from an organization’s method of protection of their data and ensuring cyber resilience. So, to recap, if everyone in the organization implements and practices a cyber-resilient lifestyle, then the organization would have a better chance of preventing future sickness of their data. However, having said this, it doesn’t guarantee an absolutely secure environment as the company operates into the digital landscape. Cyber threats have evolved in how to infiltrate or compromise systems, and as a result, organizations should continually strive to evolve and adapt their immunity to potential cyber threats as new strains of viruses, malware or hacking techniques are introduced to this landscape. With this, adding layers of security is a much more effective approach than relying solely on a single mechanism for data protection. All defense layers should work in unison to be effective and be validated throughout its lifecycle. So, what would those layers encompass?
Approach for Cyber Resiliency
Let’s start examining the layers of a company’s approach to cyber resiliency. As per the author of this article, the most important layers on which a company needs to focus are as follows:
- Full Visibility, Understanding and Up-to-date Record-keeping of current inventory or what’s connecting or connected to the company’s network, servers, databases, mobile devices, PLC’s, relays IED’s, IoT devices or simply discovery of all company’s assets
- Risk Assessment—after taking inventory of all assets connected to the company’s network, they must be evaluated, and those needing protection determined. Next, threats are to be analyzed, risks identified and assessed and tolerances to those risks determined. After that, current network architecture must be evaluated, and the need to make the network more secure when corresponding to the needs of the OT application determined.
- Penetration Test on the company’s current networks and establishing vulnerabilities and gaps. Conducting a penetration test is crucial for preventing data breaches and verifying effectiveness of the implemented security controls. For example, if a company performs a “brute force” attack as part of the penetration test, efficiency of passwords will be tested, and enforcing the use of a combination of letters, numbers and symbols with a minimum of eight characters will be included into the organization’s security compliancy procedures.
- Incident Response—have you ever tested how well your organization responds to a cyber threat and manages its aftermath? The goal is to ultimately prevent data breaches of the organization’s network. However, when the network has been breached, the organization needs to be able to contain the breach preventing it from further spreading into other areas of the network and ultimately taking down important process controls. An organizational emergency containment and recovery plan is a must for every organization and is also a crucial measure for mitigating outages and disruption in service to customers.
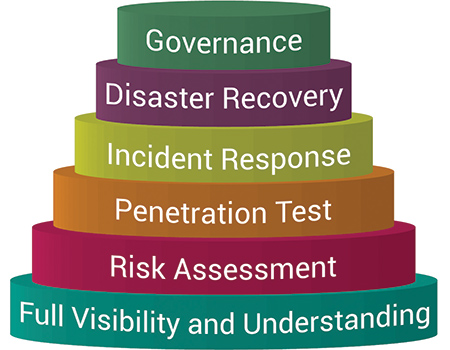
A Layered Approach to Cyber Resiliency
As per the Escal Institute of Advanced Technologies (SANS Institute), a private U.S. for-profit company that specializes in information security and cyber security training, the six key phases of an incident response plan are:
- Preparation—preparing users and IT Staff to handle potential incidents should they arise
- Identification—determining whether and if, indeed, the breach is a security incident
- Containment—limiting the damage of the incident and isolating affected systems to prevent further damage
- Eradication—finding root causes for the incident and removing affected systems from the production environment
- Recovery—permitting affected systems back into the production environment while avoiding remaining threats
- Lessons learned—completing incident documentation, performing analysis to learn from the incident and potentially improve future response efforts
- Disaster Recovery—an organization should be well prepared when situations arise. Proper procedures must be in place to prepare, react and recover from a disaster. Roles and responsibilities within the organization have to be clearly defined and communicated. The company should always have backup of their data in case of failures, and as per the best industry practices, the backup should be kept at a remote site, often referred to as a disaster recovery (DR) site. Once in a while, fire drills have to be conducted to test the effectiveness of the DR plan and modify risk tolerances accordingly while ensuring business continuity.
- Governance—compliancy within the organization typically surrounds policies, procedures and training for employees. There should be compliance controls in place so that employees are following the established organizational policies for data protection. Some compliance often is mandated by local or national authorities and regulations, and compliance with these authorities and regulations must be incorporated in the organizational compliance policies.
Outlook
In retrospect, we speak of fundamental principles that encompass a holistic view to what organizations need to consider when looking at shaping for cyber resilience in their ICS application. The company’s journey to cyber security should never stop at one singular aspect but employ an overall continuity of many moving parts. Of course, even while implementing a total security solution, nothing is absolute. Perpetual transformation, harmonizing and understanding of the needs of a converged network from both IT and OT peers while securing the environmental need to be top priority. Constant vigilance, review of new and potential threats and ongoing transformation of the organization in adapting to the ongoing threat landscape is paramount to the success of any company.
 Jonathan Azarcon is currently the EVP of marketing and product management for iS5 Communications and has more than 22 years of combined experience in telecommunications technology, working in business enterprise and industrial control applications. He has designed and implemented networks for customers worldwide as a professional services consultant with Alcatel Networks and as a VP of global services & support at RuggedCom Networks and Siemens AG as instrumental in helping customers implement & support communications technology for their ICS.
Jonathan Azarcon is currently the EVP of marketing and product management for iS5 Communications and has more than 22 years of combined experience in telecommunications technology, working in business enterprise and industrial control applications. He has designed and implemented networks for customers worldwide as a professional services consultant with Alcatel Networks and as a VP of global services & support at RuggedCom Networks and Siemens AG as instrumental in helping customers implement & support communications technology for their ICS.
References
1 United States Computer Emergency Readiness Team, Alert (TA18-074A), Russian Government Cyber Activity Targeting Energy and Other Critical Infrastructure Sectors, Last Revised March 16, 2018, https://www.us-cert.gov/ncas/alerts/TA18-074A, Last Accessed Oct 1, 2018
2 Electricity Information Sharing and Analysis Center (E-ISAC), TLP: White Paper, “Analysis of the Cyber Attack on the Ukrainian Power Grid”, Defense Use Case, March 18, 2016, Internet: https://www.nerc.com/ pa/CI/ESISAC/Documents/E-ISAC_SANS_Ukraine_DUC_18Mar2016.pdf, Last Accessed Oct 1, 2018







