The last few decades have seen major advances in technology, resulting in sig¬nificantly smaller devices, increased functionality and a new range of connectivity options. In general, the effect has been positive for everyone: Added convenience for consumers and industries alike; from online shopping and online banking, to in¬creased productivity in all industries.
For the industrial manufacturing sector, change has come rather gradually over the last decade. In some cases, the manufacturing industry still relies on infrastructures based on isolated serial communication networks to connect PLCs, RTUs and other process control equipment. Although slower than Ethernet, these often proprietary network protocols are optimized for the real time communication requirements of process control equipment, which were not possible using half duplex Ethernet. With the introduction and widespread availability of full duplex Ethernet in the late 1990s, Ethernet became a viable option for real time communication in industrial control systems. Development on modern Ethernet-based process-control protocols started during the same period, but it wasn’t until the mid-2000s that the technology was widely accepted, even for very latency sensitive process-control tasks.
The introduction of Ethernet has brought many improve¬ments to industrial control systems. Controls engineers no longer have to rely on adapters, cables and protocol analyzers for different proprietary communication pro¬tocols – a network cable and a spare network port are all that are needed for the troubleshooting and maintenance of many networked process-control devices. Common network troubleshooting tools, already well established in the IT world for years, now support this new infrastruc¬ture. In many cases, these tools are open source and free to use. Interested programmers added support for pro¬cess-control protocols to these tools, which could then be used for most troubleshooting tasks. Adding new devices to the network is now easily accomplished, assuming that the design engineer had provided enough available spare ports throughout a facility. Improvements in networking concepts always find their way into the process-control environment, resulting in higher reliability and better per¬formance. Two examples of this are the use of Ethernet redundancy protocols like Rapid Spanning Tree Protocol (RSTP) for fault tolerance and loop prevention, and the use of network time protocols for plant-wide time syn¬chronization.
In short, Ethernet has had a tremendous and mostly positive impact in the process-control landscape. However, there is a dark side. The same technology that allows for convenient online shopping from home, as well as easy and convenient connectivity within an office or a manufacturing facility, can also be used to attack the infrastructure of all connected systems using the anonymity of the internet or from the inside of a network, potentially impacting all devices within that network.
This is not a new development, though. Industry experts have long tried to stop this trend and improve security measures by publishing standards and guidelines for more secure infrastructure protection. However, application of these standards is often voluntary and not monitored for most industries.
Also, many of these standards are very generic and do not take into account the specific requirements of different industries.
Banking infrastructure, for example, places the highest priority for data protection and integrity and therefore requires significant effort regarding data encryption, while the requirements regarding communication latency and speed are relatively low. Generally, it matters little if a financial transaction takes two or five seconds to complete, as long as the transaction is secure.
For the industrial sector, the requirements are typically reversed - usually, there are no databases with sensitive information, such as personal data, social security numbers or credit card information. Instead, the communication interfaces within an industrial facility require real-time interaction between devices and are therefore very sensitive regarding latency and data throughput; a time delay of a single second during error detection can result in significant harm to personnel or equipment.
This can be visualized in the “Confidentiality, Integrity and Availability” relationship:
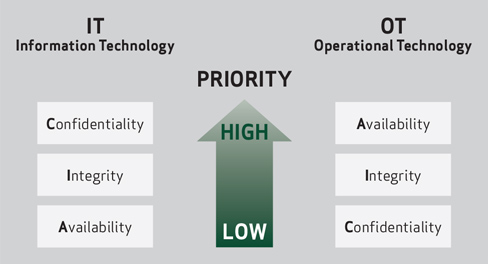
Confidentiality, Integrity and Availability
When comparing the priorities between IT and OT, it becomes obvious that a different approach is needed to protect each infrastructure. This has resulted in the development of industry-specific standards, independent of the more general standards published and maintained by IEC, ISA, ISO, NIST, etc.
For the North American Energy sector, NERC CIP is the mandatory set of standards for critical infrastructure protection and includes a wide range of topics to protect all critical cyber assets. NERC was founded in 1968 as the National Electric Reliability Council to provide voluntary operating coordination. The need for critical infrastruc¬ture protection was driven by a series of blackouts as well as several terroristic attacks, resulting in Presi¬dential Decision Directive 63 (PDD 63) in 1998, with the goal to fully protect the critical infrastructure no later than 2003. The 2001 World Trade Center attack further heightened this need, resulting in the Urgent Action Cyber Security Standard UA 1200 in 2003, which later formed the basis for the first NERC CIP standard. Shortly after¬ward, the Federal Energy Regulatory Commission (FERC) certified NERC as the Electric Reliability Organization, making all NERC standards mandatory and enforceable. The agency, which was renamed the North American Elec¬tric Reliability Council in 1981, changed its name again in 2007 to its current name, the North American Electric Reliability Corporation.
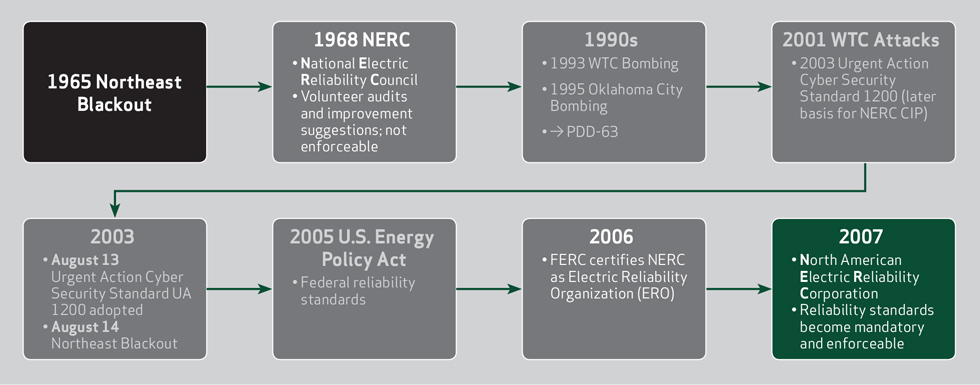
The Beginnings of NERC CIP
(click to enlarge)
Aside from CIP, NERC maintains a wide range of other standards, including EOP (Emergency Preparedness and Operations), BAL (Resource and Demand Balancing), TOP (Transmission Operations) and several more.
To clarify applicability and requirements of all NERC standards, a “Functional Model” is used. It describes each function in detail, the associated reliability tasks as well as the functional entity responsible for these tasks. These functions cover a range of 18 power industry functions, which are grouped into three functional areas:
- Standards and compliance functions
- Reliability service functions
- Planning and operating functions
Another important document is the “Glossary of Terms,” which describes specific terms in relationship to the standards documents. Without this information, the impact of some requirements might not be fully understood; an example of this will be provided when discussing the Electronic Security Perimeter (ESP).
Every NERC standard begins with an applicability list, identifying the functional entities to which the standard applies. Compliance is measured based on the definition of the reliability tasks in the Functional Model – violations occur if the reliability task assigned to a functional entity has been impaired.
Development of the standards is ongoing, with some older standards already retired while existing standards are continuously updated and new standards developed, resulting in an ongoing effort from all responsible entities to maintain standards compliance. The goal: A reliable energy infrastructure for North America.
The purpose of NERC CIP is the protection of all BES Cyber Assets – cyber assets which are a critical part of the Bulk Electric System and grouped together as BES Cyber Systems. This is achieved using three different types of controls:
- Administrative and procedural controls
- Physical access controls
- Technical controls
Since technology changes at a rapid pace, the technical controls are the most challenging requirements of NERC CIP and are the main focus of this article.
To understand the concepts and requirements of NERC CIP better, the Purdue Enterprise Reference Architecture can be used.
The original Purdue Enterprise Reference Architecture recognizes two main zones: The manufacturing zone (Levels 0 to 3, also known as operational technology) and the enterprise zone (Level 4, also referred to as information technology).
If data exchange between the manufacturing zone and the enterprise zone is required, the use of a demilitarized zone (DMZ) to separate both zones is strongly recommended. In this example, no direct communication between the manufacturing zone and the enterprise zone is possible; all communication requires data interfaces in the DMZ, which are controlled by a firewall at each border.
This basic architecture is very common for power industry facilities. The scope for NERC CIP standards in this example includes the manufacturing zone (Levels 0 to 3) as well as the firewall separating this zone from other zones.
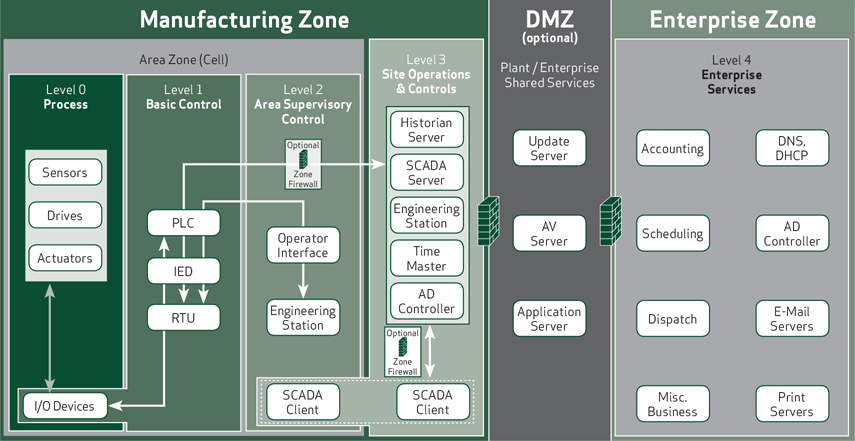
The Perdue Model: A Simplified View of the Plant Network
(click to enlarge)
Application of the NERC CIP standards is based on a list of functions and categorization criteria related to the reliable operation of the bulk electric system. Each functional entity is required to identify all associated BES Cyber Systems, resulting in an impact rating of low, medium or high. The individual NERC CIP requirements are then applied based on the impact rating of each BES Cyber System. It is possible to create multiple BES Cyber Systems, rather than treating the entire facility as single system. Depending on the system design, this can result in lower impact-rated individual BES Cyber Systems with fewer requirements and less management effort.
A central – and mandatory – figure for application of the NERC CIP standards is the entities’ CIP Senior Manager, who has the responsibility to lead the NERC CIP standards compliance effort, including the authority to delegate CIP-related tasks.
As mentioned earlier, the NERC CIP standards cover many different topics, including administrative controls and operational procedures. Examples of administrative controls are the requirements for appropriate personnel risk assessment and personnel training as well as access management and access revocation. Operational procedures need to include system recovery, incident response and information protection. Physical access control requirements cover topics from physical facility access and a visitor control program, as well as requirements for access logging.
In many cases, these topics are already common practice for industrial facilities and will not be reviewed further; the technical cyber protection requirements of NERC CIP are usually the most problematic aspect of CIP compliance. These include requirements for:
- Electronic security perimeters
- Physical as well as logical port management
- Patch management and malicious code prevention
- Security event monitoring
- System access control
- Configuration change management
- Vulnerability assessments
- Handling of removable storage devices and transient cyber assets
These requirements create several technical challenges. Frequently, there is a mix of legacy devices and modern devices on the same network – PLCs, RTUs, power meters, protection relays, remote I/O racks etc. Many legacy devices lack even basic cyber security features for access control, port management or event monitoring. In some cases, the manufacturers for these devices no longer provide firmware updates, but replacing these devices with more modern versions might require a redesign of system interfaces. Also, proprietary communication protocols might make relocation of these devices behind a firewall impossible, due to special protocol requirements.
Patch management has the potential to disrupt system operation if there are compatibility issues. Proper planning, as well as accurate system recovery procedures in case of patch failures, is absolutely critical. The same applies to active vulnerability assessment, which has the potential for devices rebooting or locking up. Again, proper planning is absolutely vital for successful vulnerability assessment, combined with a full understanding of the system design and communication interfaces. Otherwise, the results of such assessments are useless, since the relationship between open ports and communication interfaces cannot be determined.
Presently, there is no standard concept for change management for these kinds of devices, so each device has to be managed manually using the management interfaces provided by the device manufacturer and based on the capabilities and features of the device. However, there is one critical concept that connects all devices: The ESP.
The requirement for the ESP is very specific: All cyber assets connected using a routable protocol shall reside within a defined ESP. This excludes any device connected using serial communication (RS232, RS422/485), but also excludes devices that use non routable Ethernet Layer 2 communication. Presently only TCP/IP qualifies as a mainstream protocol that supports routing, which means that any device that uses an IP address has to be considered as part of the ESP. However, there is another consideration here: Impact Rating Inheritance. Although not spelled out in the CIP standards themselves, the “Glossary of Terms” describes the term “Protected Cyber Asset” as any cyber asset within an ESP which is not part of the BES Cyber System, but will inherit the impact rating of the highest-rated BES Cyber System within the same ESP. So a printer in the same ESP as critical BES Cyber Assets would receive the same impact rating and thus the same requirements regarding patch management and vulnerability assessment.
This concept can now be used to simplify the system by applying proper network segmentation. For example, by placing all printers in a designated network separated from all critical BES Cyber Assets using a firewall, these cyber assets are now part of a new ESP without BES Cyber System, thereby reducing requirements significantly.
When properly used, the concept of Electronic Security Perimeters combined with appropriate grouping into individual BES Cyber Systems of different impact ratings can result in significantly reduced management effort for non critical cyber assets.
These challenges are not unique to NERC CIP – similar problems exist everywhere in the industrial sector. What makes the power industry special is its classification as critical infrastructure, resulting in these mandatory security standards and associated audits. While a non critical manufacturing facility might choose to ignore appropriate cyber protection implementation due to the associated costs, this is not a choice for most Bulk Electric Systems. But, at its core, NERC CIP describes many common IT security concepts that help the OT landscape to become better protected and more reliable. The best approach for this integration is a strong convergence between IT and OT personnel, combined with the appropriate administrative controls and procedures.
One topic frequently neglected is the requirement for well-maintained system documentation. Combining the growing complexity of industrial control systems with the increasing security requirements of the IT interfaces within the system, good documentation is vital for plant maintenance as well as providing evidence documents during any NERC audit process.
To help with the implementation of the CIP requirements, the CIP standards provide expected measures and exam¬ples of evidence to confirm compliance, as well as expla¬nations why specific requirements were included. For a responsible entity, this leads to a better understanding of the requirements – not only to pass an audit but actually resulting in better-protected BES Cyber Systems.
Presently missing from NERC CIP are requirements regarding maintenance contingency. As industrial control systems become more complex, the knowledge required to maintain those systems increases. Typically plant uptime requirements do not allow for the training of new personnel, which can lead to problems when experienced personnel leave. Hopefully, this is something that will be considered in future CIP standards.
Maintaining a fully NERC CIP-compliant facility is a tremendous task. As technology changes, so will the CIP standards, resulting in continuous changes to BES Cyber Systems. But with its current approach, NERC CIP is certainly a standard that will continue to improve our critical infrastructure, especially when applied during the design phases of new power industry facilities. Hopefully, this will also lead to a shift in all industries, demanding better system security designs even when not specifically mandated by regulation or law.
 Jens Puhlmann is the Industrial Control Systems (ICS) security manager for Voith, North America. He has more than 20 years of experience designing, developing and implementing advanced automation systems. Puhlmann is an expert who keeps up with the ever-changing world of technology and cyber security. Recently, he became one of the first people in North America to hold the GIAC Critical Infrastructure Protection Certification (GCIP).
Jens Puhlmann is the Industrial Control Systems (ICS) security manager for Voith, North America. He has more than 20 years of experience designing, developing and implementing advanced automation systems. Puhlmann is an expert who keeps up with the ever-changing world of technology and cyber security. Recently, he became one of the first people in North America to hold the GIAC Critical Infrastructure Protection Certification (GCIP).







