7. The Digital World opens up Cyber Threats
Cyber security creates fear in our industry as mentioning NERC/ CIP compliance can lead to the wrong behavior. The information available in our utility systems is essential for advancing system performance, proactive control and improved operations and maintenance. Cyber security standards provide the framework and requirements either towards compliance or technical solutions. The educational benefits to understanding these requirements is paramount in the adoption and embracing cyber security as a key enabler to our modern monitoring and control systems.
The fact exists that substation automation, protection and control systems have changed significantly in the past decade and will continue to change with technology advancements. Systems have become more interconnected and provide end users with much more information to allow for higher reliability and greater levels of control. Interoperability between different vendor products and systems has been achieved by developing products and solutions based on open standards and by leveraging commercial technology like standard Ethernet technology. This change in technology has not only brought huge benefits from an operational point of view as discussed in the previous sections, it also permits substation automation, protection and control systems to address cyber security issues similar to other traditional, enterprise systems which have been facing the same industry challenges for years.
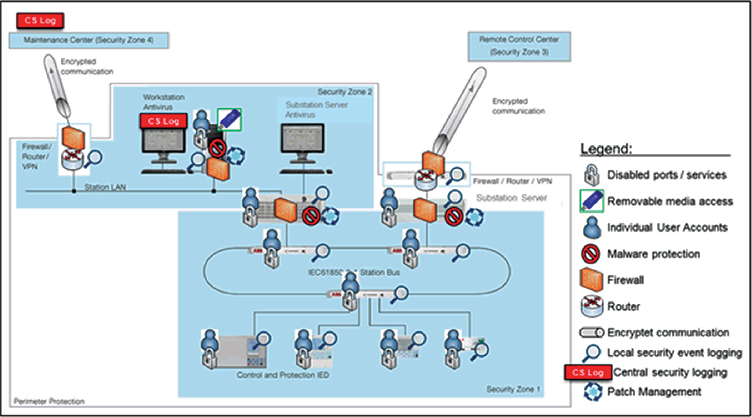
Figure 9: Example Substation Automation System Reference Architecture for Defence in Depth
(click to enlarge)
Tightly integrating the control system components and allowing inter-connected control systems with the external systems not only allows for more and faster information exchange, but, it also provides entry points for hackers and increases the need to protect against cyber-attacks. Using Ethernet and TCP/IP based communications not only make systems more interoperable, but also opened the door for trojans, worms, viruses and Internet based attacks, etc. The need for secure substation automation protection and control systems as well as the entire utility Information Technology infrastructure is being pushed in many markets by regulations to ensure national security due to the potential impact that a coordinated cyber-attack on the electric utility control system could have on wide scale outages. The key to any successful security system is deploying Defense-in-depth strategy as shown in Figure 9. Threat models are constantly changing, the bad guys are getting smarter and the monitoring and management of the overall IT systems is paramount to keep the power system control equipment safe and secure.
In addition to government driven efforts the increased importance of cyber security for power systems has also lead to various standard bodies and working groups taking on the challenging topic. The focus, level of detail and maturity of these efforts are quite broad. At the moment five initiatives seem to be most advanced, which we will discuss in the following paragraphs and should be included in your utility overall cyber security policy and practices.
7.1. NERC CIP
The NERC CIP regulations have had the biggest impact on electric utilities so far and been the focal point of most security programs. The regulation makes a clear statement that the main responsibility for securing the electric grid lies with the utilities and that it is not just about technology but also about processes. There are some shortcomings of the current version, i.e. the exclusion of serial protocols or the focus on a single electronic security perimeter. An additional area for improvement is the definition of critical assets and critical cyber assets. While the definition of what is deemed critical and what is not has been made a bit clearer within the NERC/CIP standard version 4 and 5 [17], protection of critical (cyber) assets is still done in an all or nothing fashion. If a cyber-asset is classified as critical all NERC CIP requirements apply, if it is not classified as critical then it must not be protected at all (unless it is within the electronic security perimeter).
This all or nothing approach does not take into account different levels of criticality and does not allow for different levels of security, which is a common best practice for security of computer based systems. However, the ongoing revisions are constantly looking at different levels of criticality, which will hopefully lead to a more realistic and more granular approach to cyber security. It is important to note that the NERC standards are performance based standards that inform the utility what security measures need to be implemented and monitored. Therefore, no product or technical solution can claim to be NERC CIP compliant but rather the technical solution can support the utilities compliance to these standards. On the other hand, the IEEE and IEC develop technical standards that provide the technical blueprint or the “How” for the utility security solution and the most important standards are listed below.
7.2. IEEE C37.240
Jointly within IEEE PES Substations and PSRC, this standard is based on the applicability and the technical implementation of the NERC CIP and NIST Smart Grid security efforts for substation automation, protection and control systems. The standard on “Cyber Security Requirements for Substation Automation, Protection and Control Systems” provides technical requirements for substation cyber security. It presents sound engineering practices that can be applied to achieve high levels of cyber security of automation, protection and control systems independent of voltage level or criticality of cyber assets. Cyber security includes trust and assurance of data in motion, data at rest and incident response.
7.3. IEC 62351
IEC 62351 is a technical security standard that aims to secure power system specific communication protocols such as IEC 61850 or IEC 60870-5-104. While most parts of the standard have been released in 2009 more work is needed before systems compliant to IEC 62351 can be put on the market. First of all, the affected communication standards must be changed to support IEC 62351. In addition there are some technical challenges with securing real time traffic that must be addressed by the working group of IEC 62351.
7.4. IEEE 1686
Security of intelligent electronic devices is the scope of IEEE 1686. The document defines in technical detail security requirements for IED’s, e.g. for user authentication or security event logging. The standard very nicely points out that a) adherence to the standard does not ensure adequate cyber security, i.e. that adherence to the standard is only one piece in the overall puzzle, and that b) adherence to every clause in the standard may not be required for every cyber security program. With this the standard gives vendors clear technical requirements for product features but at the same time leaves room for specific, tailored system solutions at the customer site.
Summary Benefits of the Digital Substation
A fully digital substation is smaller, more reliable, has a reduced life-cycle cost and is simpler to maintain and extend than an analog one. It offers increased safety and is more efficient than its analog equivalent. Not every substation needs to be catapulted into a wholesale digital world – it depends on the substation size and type, and whether it is a new station or a retrofit of the secondary system. Different approaches and solutions are required. Flexible solutions allow utilities to set their own pace on their way toward the digital substation.
- Increased system availability by replacing of electromechanical, static or old fashioned digital secondary equipment with modern numerical devices bundled to a real-time communication network and connected to a higher level system such as a substation automation system or SCADA, allows continuous monitoring of all connected secondary equipment.
- Increased system and personnel safety utilizing remote control combined with authority and rule-based access and remote testing, allows increased system safety and security. Personnel safety is increased since more tests can be done without putting the test personnel close to primary equipment or without the risk of inadvertently opening current transformer (CT) circuits.
- Increased functionality with a fully distributed architecture coupled with un-restricted communication and process capability enables the system to add new functions easily with zero or minimal outage time, giving the user additional benefit with respect to safe and secure system.
- Interoperability through deployment of IEC 61850 compliant solutions, interoperability with regard to communications with other manufacturer’s equipment can be achieved. The benefit is IEDs from different suppliers can be mixed on the same bus without concern for communication incompatibilities.
Conclusion
Technology has changed significantly from over the past 30 years and will continue advance enabling more benefits from The Digital World. The early adoption of microprocessor relays started the era into The Digital World. Along with their significant advantages, they also introduced our world to software and communicating devices to the realm of Cyber Threats in our changing environment. The introduction of the IEC 61850 station and process bus standards for substations has provided a platform that all manufactures can develop upon to achieve the overall goal of interoperability.
John Burger’s visionary ideas are being realized with the technology available today. In addition to the interoperability benefits, footprint of primary switchgear reduction using sensors (NCIT) replacing conventional measuring transformers and breaker controls allows a much safer work environment and a massive reduction of cabling by going from a lot of copper cables to a few fiber optic communication cables. As for the challenges presented by the cyber threats, the industry must embrace modern device capabilities to deter, delay and detect the bad guys. Let us not forget that the multifunction relay is today the source of information that can enable higher level systems to be proactive in the overall power system stability. Most importantly, the “R” in NERC means reliability so while CIP standards might drive organizations to shutdown communication access to the substation information, it is so crucial that the substation data be accessible to higher level systems.
About the Authors
 Stefan Meier has been working with ABB Switzerland for more than 15 years. He held several positions, from commissioning of substation automation systems, through technical support and project management. Today he is a global product manager for process bus solutions, where he coordinates the introduction IEC 61850 process bus in pilot and commercial projects. Stefan studied electrical science at the University of Applied Sciences Northwestern Switzerland, and holds a master degree in business administration from Edinburgh Business School of Heriot-Watt University, Scotland.
Stefan Meier has been working with ABB Switzerland for more than 15 years. He held several positions, from commissioning of substation automation systems, through technical support and project management. Today he is a global product manager for process bus solutions, where he coordinates the introduction IEC 61850 process bus in pilot and commercial projects. Stefan studied electrical science at the University of Applied Sciences Northwestern Switzerland, and holds a master degree in business administration from Edinburgh Business School of Heriot-Watt University, Scotland.
 Steve Kunsman is a recognized Substation Automation Specialist with over 32 years in substation automation, protection and control applications, communications technologies (IEC 61850 and DNP), cyber security for substation automation, and the Relion product family of protection and control relays. His ABB career began in 1984 as an Electrical Designer for the protective relay group and has held various engineering, technology and product management positions within the North American and global substation automation organizations. Steve holds a B.S. in Electrical Engineering from the Lafayette College in Easton, Pennsylvania and an MBA in management of technology from Lehigh University in Bethlehem, Pennsylvania.
Steve Kunsman is a recognized Substation Automation Specialist with over 32 years in substation automation, protection and control applications, communications technologies (IEC 61850 and DNP), cyber security for substation automation, and the Relion product family of protection and control relays. His ABB career began in 1984 as an Electrical Designer for the protective relay group and has held various engineering, technology and product management positions within the North American and global substation automation organizations. Steve holds a B.S. in Electrical Engineering from the Lafayette College in Easton, Pennsylvania and an MBA in management of technology from Lehigh University in Bethlehem, Pennsylvania.
References
- S. Meier, “Enabling digital substations,” in ABB Review, 4/2014
- T. Werner, S. Meier, “Performance considerations in digital substation applications”, PACWorld conference Glasgow, 2015
- IEC 60831, “Teleprotection equipment of power systems – performance and testing – Part 1: Command Systems,” IEC, Tech. Rep., 1999
- IEC 62271-100, “High-voltage switchgear and control gear – Part 100: Alternating-current circuit-breakers”, IEC, International standard, 2012
- “The Grid Code, Issue 5,” National Grid Electricity Transmission plc., Revision 13, 2015 “Protection System Reliability”, “A technical paper”, NERC System Protection and control taskforce, 2008
- J. Widmer, Cigré paper B3-211 “From IEC 61850 based substations with sampled values to billing metering”, Cigré Session Paris, 2014
- D. Fuechsle, M. Stanek, GCC Power paper “Experiences with Non-Conventional Instrument Transformers (NCITs)”, GCC Power, 2009
- • IEC 61850-5, “Communication networks and systems for power utility automation – Part 5: Communication Requirements for Functions and Device Models,” IEC, International standard, 2013
- IEC 61850-10, “Communication networks and systems for power utility automation – Part 10: Communication Requirements for Functions and Device Models,” IEC, International standard, 2013
- IEC 60044-7, “Instrument transformers – Part 7: Electronic voltage transformers”, IEC, International standard, 1999
- IEC 60044-8, “Instrument transformers – Part 8: Electronic current transformers”, IEC, International standard, 2002
- “Implementation Guideline for Digital Interface to Instrument Transformers using IEC 61850-9-2”, published by UCA International Users Groups, 2004
- IEC 61850-90-4, “Communication Networks and Systems for Power utility automation - Part 90-4: Network Engineering Guidelines,” IEC, Tech. Rep., 2013
- S. Kunsman, N. Price, et al, “Protection and Control System Utilization of NCIT & Process Bus”, PACWorld conference Raleigh, 2015
- S. Kunsman, M.Braendle, et al, “Replacing Fear with Knowledge - Cyber Security for Substation Automation, Protection and Control Systems”, 69th Annual Georgia Tech Relay Conference, 2015
- “Implementation Study Final Report CIP Version 5 Transition Program”, NERC Website, October 2014







