Currently, the nation’s power system consists of both legacy and next generation technologies. This increased digital functionality provides a larger attack surface for any potential adversaries, such as nation-states, terrorists, malicious contractors, and disgruntled employees. The U.S. federal government has responded to all of these changes in technology and the threat environment by developing and updating cyber security guidance. Utilities are dedicating significant resources to understand the guidance and determine what is applicable. For many utilities with limited cyber security technical expertise, attempting to understand and implement all this guidance is daunting. EPRI initiated a project last year, not to develop a new guidance document, but to assist utilities in navigating all the diverse existing guidance that is applicable to the electric sector that resulted in three new reports:
- Risk Management in Practice – A Guide for the Electric Sector 1
- Security Posture using the Electricity Subsector Cybersecurity Capability Maturity Model (ES-C2M2) 2
- Cyber Security Risk Management in Practice – Comparative Analyses Tables 3
New grid technologies are introducing millions of novel, intelligent components to the electric grid that communicate in much more advanced ways (two-way communications, dynamic optimization, and wired and wireless communications) than in the past. These new components will operate in conjunction with legacy equipment that may be several decades old and provide little to no cyber security controls. In addition, with alternative energy sources such as solar power and wind, there is increased interconnection across organizations and systems. With the increase in the use of digital devices and more advanced communications, the overall cyber risk has increased. For example, as substations are modernized, the new equipment is digital, rather than analog. These new devices include commercially available operating systems, protocols, and applications with vulnerabilities that may be exploited.
Address a constantly changing environment
Some utilities have the technical expertise to assess and use the various documents as part of an overall cyber security risk management program. However, not all utilities have in-house expertise and must rely on external organizations and guidance. In addition, some utilities are being asked by management and by regulatory organizations, such as state public utility commissions (PUCs), to demonstrate how they meet the requirements and/or content of these various documents. Currently, responding to these requests is difficult because there is no overarching guidance that tells utilities how to get started.
To address this constantly changing environment – including new technology, threats, guidance, and regulations, EPRI initiated a collaborative effort with DOE, utilities, the trade associations, Carnegie-Mellon University, and researchers. The goal was to assist utilities in assessing and applying the various cyber security documents, rather than developing new guidance.
Follow the flowchart
The first task was to develop a flowchart (Figure 1) that related the guidance and methodologies of an enterprise risk management process and strategy, focusing on cyber security. All the new cyber security guidance needs to be included in the context of an overall enterprise risk management process and strategy. The following flowchart has been used by utility cyber security staff in meetings with management, to provide an overview of cyber security.
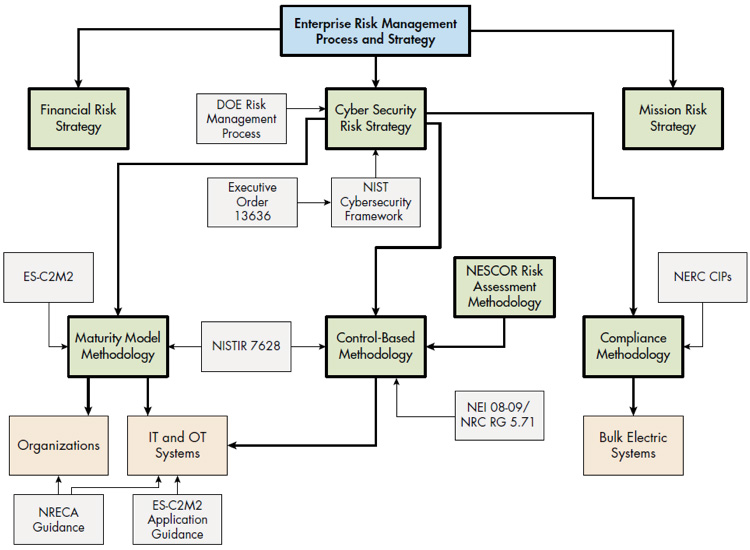
Figure 1 Risk Management Guidance Flowchart
Standardize the guidance and make it free
The second task was to provide a comparative analysis of the referenced documents. All of the documents included in the diagram are at different levels of specificity and may be used for different purposes related to managing cyber security risk. For example, the ES-C2M2 may be used to determine the maturity level of an organization and the National Institute of Standards and Technology Interagency Report (NISTIR) 7628 security requirements may be used as part of a cyber security risk assessment of specific control systems.
Currently, there are many versions of the comparative analysis—developed by utilities and contractors. The goal of the EPRI project was to have a common baseline set that is publicly available at no cost and may be used by everyone. The focus of the documents is to provide guidance on applying the diverse existing cyber security guidance that is applicable to the electric sector. The security posture document provides guidance for performing a maturity assessment on systems using the DOE ES-C2M2. Application guidance is included to assist utilities in this system assessment and NISTIR 7628 security requirements are allocated to specific practices within the ten domains. All three documents provide a framework and comparative analyses of existing guidance that may be used by cyber security practitioners in addressing cyber security.
The road ahead
These first versions are not intended to be final—and the goal is to have people use the comparative analysis tables included in documents and provide comments for future versions.
However, we’ve already heard from our utility members that the standardized guidance has allowed their business units to identify risks, map risk decisions to mitigate outcomes, and model risk by mapping potential impact. We’ve also heard that this work has helped utility employees answer a critical question: Which documents do I need for my cyber security efforts, and where do I start?
About the Author
 Annabelle Lee is a Senior Technical Executive in the Power Delivery and Utilization Sector of the Electric Power Research Institute (EPRI). She provides technical oversight to the various projects within the Cyber Security and Privacy Program at EPRI. Her current technical focus is on applied cryptography, security specifications, and cyber security risk management and metrics. Annabelle’s experience comprises more than 35 years of technical experience in IT system design and implementation and more than 25 years of cyber security specification development and testing. Over her career she has authored or co-authored many documents on cyber security, cryptography, and testing. She began her career in private industry concentrating on IT systems specifications, software testing, and quality assurance.
Annabelle Lee is a Senior Technical Executive in the Power Delivery and Utilization Sector of the Electric Power Research Institute (EPRI). She provides technical oversight to the various projects within the Cyber Security and Privacy Program at EPRI. Her current technical focus is on applied cryptography, security specifications, and cyber security risk management and metrics. Annabelle’s experience comprises more than 35 years of technical experience in IT system design and implementation and more than 25 years of cyber security specification development and testing. Over her career she has authored or co-authored many documents on cyber security, cryptography, and testing. She began her career in private industry concentrating on IT systems specifications, software testing, and quality assurance.
References
1 http://www.epri.com/abstracts/Pages/ProductAbstract.aspx?Productld=000000003002003333
2 http://www.epri.com/abstracts/Pages/ProductAbstract.aspx?Productld=000000003002003332
3 http://www.epri.com/abstracts/Pages/ProductAbstract.aspx?Productld=000000003002004712







