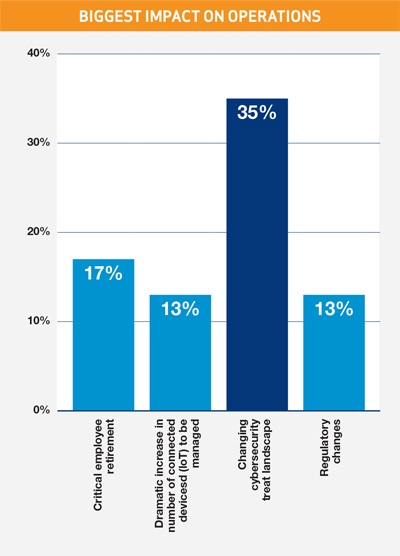
There is nary a day that passes that the risk of, or worse yet the perpetration of, a cyber-attack doesn’t play out across the headlines. It is no surprise then that the recently released 2018 BRIDGE Index™ Survey on Grid Security revealed that utility operations professionals across IT and OT rated the changing cybersecurity threat landscape as having the biggest impact on operations. In fact, so great the concern, it ranked twice as high as all other major industry shakeups, including critical employee retirements, and nearly four times as high as the impact from the emergence of distributed energy resources.
The concern is well founded. Hackers are organized, well-funded and are not restricted in their thoughts or techniques; neither do they have to abide by laws. This gives them a significant advantage over the good guys who are trying to protect the real-time operations of our power grid while managing their ‘day job’. In addition, new technologies, such as those driven by grid modernization, and the ever-changing regulations, make it even harder to stay ahead of the hackers.
With the odds seemingly stacked unfavorably against the utilities, inspiration may be found in the history books. Faced with defeating a superior enemy, many a leader has credited the ability to creatively out-think one’s enemy as the turning point to their success. Leveraging this lesson, utilities must shift from a compliance first approach that places them in a reactive position. Instead, utilities must outthink their would-be enemies by developing a strategic approach that addresses both compliance and security on a holistic, ongoing basis.
History and Today
Recent developments show that bad actors, some with the support of foreign governments, continually seek new areas of access. While NERC-CIP standards are ever improving, unfortunately so too are the techniques of these would-be hackers whose goal is to undermine the grid. Considering this, it is not sufficient for utility organizations to continue as they have been. For example, compliance driven security measures such as providing employees training on how to secure laptops, thumb drives and physical facilities such as substations or control centers, will not alone ensure the safety of the national power grid. What’s needed is an overarching flexible security strategy that encompasses a series of foundational steps evolving as needed to protect the real-time operations of the grid.
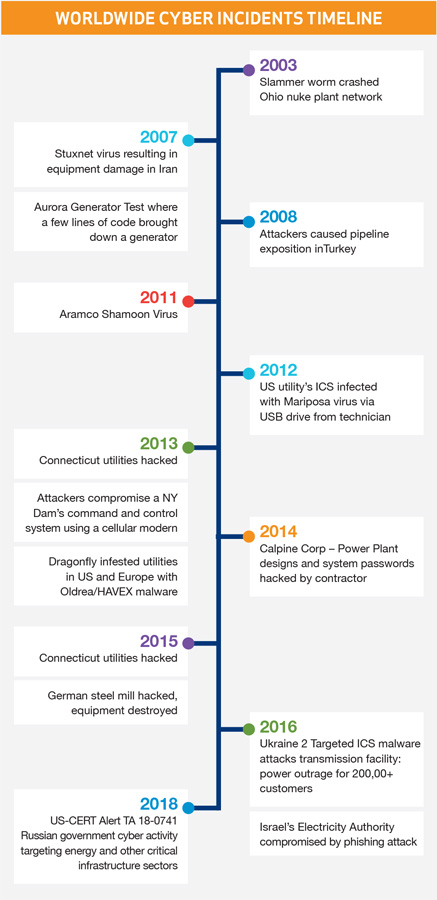
A foreshadowing of what’s likely to happen if we remain on our current path, occurred in December 2015, in an overseas grid control center where operators watched helplessly as their cursors moved across their computer displays, clicking substations offline. They frantically struggled to retake control until being involuntarily logged out. By the time the cyber-attack ended, three stations were seized and over 225,000 electricity customers lost power. The hackers also shut down the three centers’ uninterruptible power supplies (UPS), leaving even the operators themselves in the dark.
In March 15, 2018 headlines announced that Russia had infiltrated the U.S. Power Grid based on a joint report from FBI and Department of Homeland Security (DHS) report claiming Russian hackers had gained access to computers collecting sensitive data including passwords, logins, and information about energy generation.
The financial impact of similar kinds of attacks in the U.S., rose to $5 billion in 2017 and the monthly attack rate in 2017 was 10 times the rate of attacks in 2016.
The U.S. power grid is one of the 16 critical infrastructure sectors monitored by the DHS as essential to our nation’s well-being, and is naturally considered a high-value target to those that seek to harm the U.S. According to an IBM report (Year in Review: How Did the Cyber Threat Landscape Change in 2017), “dozens of U.S. power companies were compromised in 2017, with some attacks causing shutdowns and disruption of distribution. Attackers took over systems that controlled valves, pipes and conveyor belts in what may have been experimental activities or mere displays of what they could accomplish with a full-scale attack.”
You Can’t Afford to Wait. You Can’t Afford to Act, Either
The nature of the utility business is continually evolving. Distributed Generation at the Grid Edge is becoming the norm as well as development of distributed energy resource management systems that connect consumers into a utility’s grid management system. While there are many benefits to these changes, it also broadens the attack surface for threats to the power grid.
Almost five years ago, Louise Downing and James Polson warned in the article, “Hackers Find Open Back Door to Power Grid with Renewables,” published by Bloomberg Business, that “the communication networks and software that link green energy sources to the grid (as well as the electronic meters) that send real time power usage to consumers and utilities, are providing new back-door entry paths for computer hackers to raise havoc with the grid.”
There are many governing bodies and even more rules and regulations that are trying to help address these types of risks. And while this has helped, the bar is not being set high enough or measures deployed fast enough. This is complicated by the fact that for the majority of those who work in utility companies, their time available for strategic security and compliance thinking or actions is very limited. Even those whose primary responsibilities are security and compliance find themselves in tactical response mode more than 90% of their time.
Given the challenges and the limited resources to solve this problem, is it hopeless? Simply put, no! While there is no silver bullet to providing security, there are concrete strategies and actions that can be taken by utility organizations to reduce the risk. It is critical to note that this isn’t a discreet, one-time task. In the same manner as utilities continue to address safety issues, security must be managed on a continuum basis. In fact, security should be a series of flexing strategies with adaptive focus and ongoing tasks that impact every employee, supplier, process and technology. This is the only true design to reduce the risk of compromise for the power grid.
Credit: BRIDGE Energy Group
Why Change Now?
In summary, there are four primary drivers of the need to act now:
- Exponentially more risks - Collectively as an industry, we have broadened the cyber-attack surface all the way to the home. The intelligent electronic devices (IEDs) inside the customer dwelling are, in many cases, not under the direct control of the utility. And as the grid’s edge becomes increasingly populated with these IEDs such as inverters, grid controllers, battery control devices and more, the types, forms and numbers of vulnerabilities utilities are dealing with will continue to multiply.
- Increasingly dynamic threats - As an industry, we are increasingly aware of advances in the development of malware targeted at our SCADA / EMS (and other ICS) systems and perhaps even more frightening, is the vulnerability that the supply-chain of these systems represents. This was highlighted by the January 2018 DHS announcement describing Russian government cyber hackers’ activities using the supply-chain vector to conduct network reconnaissance, move laterally and then collect information about Industrial Control Systems (ICS).
- Compliance first focus gives hackers the advantage - The utilities’ response has been to solve the immediate problems. Point-solutions and reactive activities abound. Compliance requirements are addressed with heavy employee burdens driven by repetitive, yet knowledge-based tasks. Security threats and alerts are often met with stop-gap measures and solutions. When strategic capabilities are deployed, the number of stakeholders and the incredibly federated models for disbursement of accountability, resulting in a lack of effectiveness and efficiencies and increased employee burden.
- Increasing security and compliance costs - According to the recent 2018 Grid Security Survey, more than 47 percent of the respondents have a major compliance project planned in the next 24 Months. Clearly, CIP Compliance expenditures continue to increase. After more than10 years of CIP Compliance, it is surprising that utilities have not yet fully assimilated compliance concepts into their cybersecurity programs to reduce costs and exposure to change. Utilities routinely declare that they cannot afford CIP+, but they can and should adopt strategic cybersecurity policies that drive sustainable compliance solutions.
To Win Long-Term, More Strategic Thinking is Needed
The 2018 Grid Security Survey also revealed that utilities are still concerned about the lack of IT/OT alignment, compliance burdens, cybersecurity and the learning curve for IT. These concerns take on increasing importance and must be addressed for utilities to take full advantage of the digital grid. A strategic security and compliance approach must be taken to address these concerns and proactively address risk and cost.
Utility leaders must take the following actions:
- Integrate – Assimilate compliance concepts and requirements into your security program making security and thus – compliance – a strategic element of business. You already have “Safety Moments.” It is time to introduce “Security Moments” as well. This will raise awareness, demonstrate importance and immediately drive the enterprise into a more proactive mode in all aspects of operations and planning, including budgets, resource allocation and accountability.
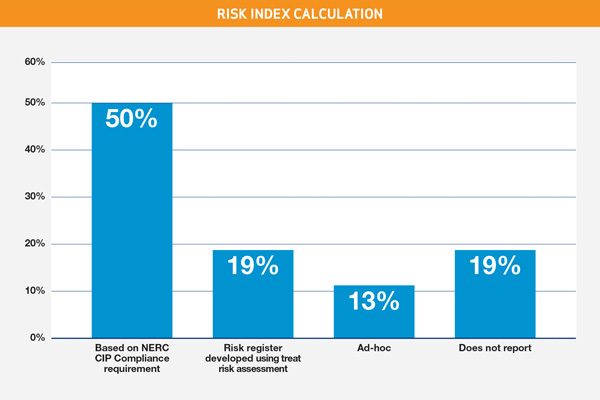
- Prioritize – Manage both security and associated compliance activities using a risk perspective. The Grid Security Survey results indicated that more than 30 percent of respondents did not report on real-time operations risk or do it on an ad-hoc basis. However, a risk register using a threat risk assessment is needed to give adequate insight into the true risk to drive prioritization. You should establish and leverage objective measures, on-the-ground personnel and security expertise, to gain insight into the effectiveness of your work. Your program should have the ability to flex, repurpose, reorganize and refocus, based on changing priorities.
- Drive Continuity – As part of your overarching security strategy, effective and continuous action for compliance is critical. It must also be informed through an approach that provides a holistic status and understanding of the multitude of interconnected activities required. With limited resources to tap and budget demands at an all-time high, this strategic approach requires a creative solution that considers the impact on your people, makes use of your established processes and in-place technologies, reduces audit preparation time and drives proactive, not reactive actions. In compliance language, this means not only understanding what compliance state you are in today but also having a certain level of assurance as to whether you will be compliant tomorrow or are ready for the audit next year.
Credit: BRIDGE Energy Group
Credit: BRIDGE Energy Group
Conclusion
Last month’s announcement by NERC of their findings of cyber breach against a WECC utility and the subsequent assessment of a $2.7 million fine again highlights what is on the line for utilities, customers, and shareholders. As consumer expectations evolve and advanced grid management schemes become a reality, operating the U.S. power grid in a secure and compliant manner means considering associated Internet-of-Things (IoT) connectivity and other open communication networks. It doesn’t take much imagination to understand that this is increasing the potential for a cyber-attack that might easily cripple a broad swath of the U.S. economy.
While regulations will continue to evolve, raising the preparedness of the industry as a whole should be the focus. As such, these regulations cannot match the pace of the increasing sophistication of the threats and the focus of the bad-guys. Utilities cannot rely on compliance with standards as their security strategy. Cybersecurity strategies and their associated compliance requirements are critical business elements, and not just an IT issue. There is no mystique to good security! Through simplifying programs, prioritizing actions based on risk and internalizing the need for continuous vigilance and actions, we can and will meet the security challenges of the future.
 Richard Jones, VP Grid Security at BRIDGE Energy Group, is a recognized thought leader in Cybersecurity, NERC CIP and general utility regulatory compliance and reporting with over 25 years of energy and utility industry experience providing business, technology and management consulting based services. Prior to joining BRIDGE, Richard held a number of security leadership positions with the big 5 and industry focused consulting firms.
Richard Jones, VP Grid Security at BRIDGE Energy Group, is a recognized thought leader in Cybersecurity, NERC CIP and general utility regulatory compliance and reporting with over 25 years of energy and utility industry experience providing business, technology and management consulting based services. Prior to joining BRIDGE, Richard held a number of security leadership positions with the big 5 and industry focused consulting firms.







