In recent years the number of cyberattacks directed at energy installations, including power utilities has increased dramatically. I discussed this in my article ‘Securing Utilities from Cyberattacks - For the times they are a-changin' in the November/December 2012 issue of this magazine.
As a result, cyber security has become big business for the power industry. A recent report from research firm Zpryme estimates that between now and 2020 overall United States utility spending on cyber security will total $7.25 billion.
So what is the best way to defend your power infrastructure in this new era of escalated cyber threats? In this article I will explain how ‘zones and conduits,’ a concept included in ISA/IEC 62443 standards (formerly ANSI/ISA-99 standards), can help create a secure environment.
SCADA Security Challenges: Interconnectedness and Isolation
There are two opposing trends impacting substation control network design today.
The first trend is toward greater ‘interconnectedness’ of the entire grid. The ability for information to flow all the way from the smart meter at the customer’s premises to the utility’s management team is part of the attractiveness of modern networking technologies. Today, the information flow is largely one way, but we all know that one of the promises of the smart grid is to also feed data (and possibly controls) back down to the smart meter to improve the efficiency, reliability, and sustainability of the energy infrastructure.
The second trend is the desire to secure the grid by ‘ring fencing’ the bulk electrical system behind an ‘electronic security perimeter’ (ESP) as recommended by the North American Electric Reliability Corporation’s (NERC) Critical Infrastructure Protection (CIP) program.
I am on the record as saying that I don’t believe these bastion (single line of defense) models of security work today. What the Stuxnet worm showed us is that there are multiple pathways to sensitive equipment – pathways that don’t require a connection to the Internet. You can read more about this in ‘How Stuxnet Spreads.’
The reality of multiple pathways is also supported by work done by the U.S. Department of Homeland Security. They have stated:
“In… hundreds of vulnerability assessments in the private sector, in no case have we ever found the operations network, the SCADA system or energy management system separated from the enterprise network. On average, we see 11 direct connections between those networks. In some extreme cases, we have identified up to 250 connections…”
With the help of Murphy’s Law, eventually all single point solutions are either bypassed or experience some sort of malfunction, leaving the system open to attack. A better solution is ‘Defense in Depth’ (DiD). In this model, the control system is protected by multiple layers of defense that are distributed throughout the control network.
This doesn’t mean that boundary protection is not important – it certainly is. But this boundary protection must also be backed up by additional layers of defense

Often it is easier and less expensive to secure a conduit than the assets at the end of it.
Defense in Depth is Key to SCADA Security
DiD is a best practice that is commonly used in the IT world. Rather than hiding the company behind a firewall, leading companies are starting to break their IT systems into defensible zones based on criticality. This white paper by Verizon on Network Segmentation and DiD describes the concept well:
Traditional network security has been based on separating the enterprise internal network from all external connections and controlling what is allowed to enter. This plan cannot deliver effective security in today’s enterprise networks. It is based on the assumption that all the “good guys” are inside the company and all the “bad guys” are outside. In practice, this assumption is never true. While bad guys sometimes manage to penetrate the castle defenses, most attacks are traced to the computers of insiders. Even with the best of intentions, any employee might be fooled by an e-mail, web page, or instant message containing a virus attachment— turning at least their computer, if not the employee, into a temporary bad guy.
If a traditional ‘perimeter defense’ cannot protect today’s enterprise, what can? Security-conscious enterprises are turning to fine-grained segmentation. This strategy, although focused on defense against cyberattacks, also pays dividends in terms of network flexibility and interactions with business partners. Segmented networks are orderly, carefully defined networks.
In the industrial SCADA world, this particular layered defense strategy is known as the zone and conduit network segmentation model. It is a core requirement of the in the ISA/ IEC 62443 standards for Security for Industrial Automation and Control Systems.
ISA IEC 62443 Zones and Conduits
One layer of defense is to eliminate ‘flat’ networks and segment them according to the zone and conduit model that is included in ISA/IEC 62443. This model provides a way to segment and isolate the various subsystems in a control network.
A zone is defined as a grouping of logical or physical assets that share common security requirements, based on factors such as criticality and consequence. Equipment in a zone has a security level capability. If the capability level does not meet or exceed the requirement level, then extra security measures – such as implementing additional technology or policies – must be taken.
Any communication between zones must be via a defined conduit.
Conduits control access to zones. Conduits also resist Denial of Service (DoS) attacks or the transfer of malware, shield other network systems, and protect the integrity and confidentiality of network traffic. Typically, the controls on a conduit mitigate the difference between a zone’s security level capability and its security requirements, particularly when older, less secure components are still in service. Focusing on conduit mitigations is often more cost-effective than having to upgrade every device or computer in a zone.
The zone and conduit approach starts with defining groups of systems and assets that share common functionality and common security requirements. These groups are the zones that require protection.
For example, the first division might be operational areas, such as regions or substation types, with secondary functional layers defined, such as Supervisory Level, Station Level and Bay Level. Zones can also be defined according to an asset’s inherent security capabilities. For example, older IEDs that have weak authentication (i.e., poorly designed password controls) could be grouped into a zone that provides them with additional defenses.
A conduit should then be defined in terms of:
- The zones it connects
- The communications technologies it uses
- The protocols it transports
- The security features it needs to provide to its connected zones
Typically, determining the information transfer requirements between zones over the network is straightforward. Tools like traffic flow analyzers or even simple protocol analyzers can show which systems are exchanging data and the services they are using.
It is also wise to look beyond the network, to determine the hidden traffic flows. For example, are files ever moved via USB drive? Do employees connect to outside resources using a dialup modem? These flows are easy to miss, but can result in serious security issues if not managed carefully.
Types of Conduit Controls
There are several options for implementing security technologies on a conduit, two of the most popular ones being industrial firewalls and virtual private networks.
Case Study: Using Zones and Conduits to Secure a Distributed Electronic Security Perimeter (ESP)
By Eric Byres
A large utility had an agreement with several industrial customers to buy and sell power. This required real-time communications between the utility substations and third-party facilities for power quality metering. The utility owned the metering equipment, but it sat in another company’s premises, making the definition of an ESP fuzzy.
If inside the ESP, the demands for physical isolation and auditing were unrealistic. If outside, the traffic needed to be routed through the ESP firewall, adding complexity and risk. There was also the issue of how to manage any connectivity supported by third-party network elements.
Fine-grained control of SCADA traffic between the customer and the utility could not be assured by standard IT firewalls; these can only deny the SCADA protocol in use and cannot filter it for specific content. This potentially allows dangerous functions, such as programming commands or malformed SCADA messages, to be injected from the client site into the utility’s control systems as part of the permitted data stream.
The solution was to assume that the power meters were residing in a separate security zone that was outside of the utilities direct control. To provide adequate security, the conduits between the third parties’ facilities and the utility needed three attributes: encryption of messages, authentication of the end points and fine-grained inspection, and filtering of all SCADA messages.
An industrial firewall was installed as a conduit at each end of the utility-to-customer-link. These firewalls were configured so that only read commands (and corresponding reply messages) were permitted over a VPN tunnel. The VPN tunnel also authenticated all connections and encrypted all traffic.
This solution ensured that only specific firewalls and associated control devices could connect to each other. All other attempts to connect to either the utility or client site would be blocked – as would any attempts to write data or send programming commands.
All traffic was encrypted, ensuring that messages could not be injected midstream. Finally, the security devices provided alerts for blocked SCADA messages or suspicious connection attempts.
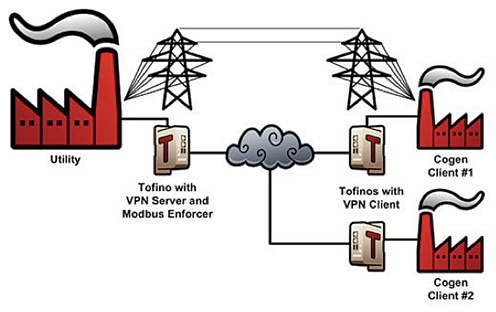
Industrial Firewalls (Tofino Security Appliances and Loadable Software Modules) act as conduits to secure cogeneration facilities.
Industrial firewalls control and monitor traffic to and from a zone, comparing the traffic passing through to a predefined security policy, and discarding messages that do not meet the policy’s requirements.
Typically they are configured to allow only the minimum traffic required for correct system operation, blocking all other unnecessary traffic and filtering out high risk messages – such as programming commands or malformed messages that might be used by hackers.
These firewalls are designed to be very engineer-friendly and are capable of detailed inspection of SCADA protocols such as DNP-3, Ethernet/IP and Modbus/TCP.
Virtual Private Networks (VPNs) are networks that are layered onto a more general network, using specific protocols or methods to ensure ’private‘ transmission of data. VPN sessions tunnel across the transport network in an encrypted format, making them ‘invisible’ for all practical purposes.
Combining DiD and Zones and Conduits Strategies
DiD, that is multiple layers of defense distributed throughout the control network is one of the best ways to defend against today’s cyber threats. Network segmentation using zones and conduits as defined by ISA IEC 62443 standards is an important element of a DiD strategy.
I strongly recommend you become proficient with segmenting your control networks for zones and conduits, and with appropriate industrial security solutions. Doing so will greatly assist your organization in mitigating threats from ‘interconnectedness’ and ‘Son-of- Stuxnet’ malware.
For a more detailed discussion about the zone and conduit model, download the White Paper “Using ANSI/ISA-99 Standards to Improve Control System Security” from the Tofino Security website. (http://web.tofinosecurity.com/download-the-white-paper-using-ansi-/-isa-99-standards-to-improve-control-system-security).
About the Author
 Eric Byres, P. Eng. and ISA Fellow, is recognized as one of the world’s leading experts in the field of SCADA security. His technical knowledge combined with his background as a process controls engineer have been indispensable in his role as CTO and VP Engineering for Tofino Security a Belden brand. He has written extensively about the malware Stuxnet. Eric founded the British Columbia Institute of Technology (BCIT) Critical Infrastructure Security Centre and shaped it into one of North America’s leading academic facilities in the area of SCADA cyber-security. For his efforts, Eric was awarded a SANS Institute Security Leadership Award in 2006. He is a notable contributor to industry standards and is Chair of the ISA99 Security Technologies Working Group and Chair of the ISA99 Cyber Threat Gap Analysis Task Group. Eric is Canadian representative for IEC TC65/WG13, a standards effort focussing on an international framework for the protection of process facilities from cyberattack.
Eric Byres, P. Eng. and ISA Fellow, is recognized as one of the world’s leading experts in the field of SCADA security. His technical knowledge combined with his background as a process controls engineer have been indispensable in his role as CTO and VP Engineering for Tofino Security a Belden brand. He has written extensively about the malware Stuxnet. Eric founded the British Columbia Institute of Technology (BCIT) Critical Infrastructure Security Centre and shaped it into one of North America’s leading academic facilities in the area of SCADA cyber-security. For his efforts, Eric was awarded a SANS Institute Security Leadership Award in 2006. He is a notable contributor to industry standards and is Chair of the ISA99 Security Technologies Working Group and Chair of the ISA99 Cyber Threat Gap Analysis Task Group. Eric is Canadian representative for IEC TC65/WG13, a standards effort focussing on an international framework for the protection of process facilities from cyberattack.







