In recent years, the electric energy industry has witnessed a new era of digitization and IT/OT convergence that brings significant efficiency and productivity benefits to asset owners.
At the same time, the deployment of large numbers of “smart” IoT/OT devices — along with pervasive connectivity between IT and OT networks that were previously “air-gapped” — significantly increases the attack surface and risk of cyberattacks. This cyber risk translates directly into business risk in the form of potential production outages, safety and environmental incidents and theft of sensitive intellectual property.
Unlike standard desktops and servers, IoT/OT devices don’t support agents and are often unpatched, unmanaged and invisible to IT teams, making them soft targets for adversaries seeking to disrupt production facilities or gain access to corporate networks.
Further increasing risk, many of the legacy OT devices and protocols previously deployed in industrial control system (ICS) and SCADA environments (HMIs, PLCs, etc.) were developed decades ago and are insecure by design, lacking modern controls such as strong authentication, encryption and hardened operating systems.
In the event of an incident involving complex cyber physical systems (CPS), regulators and corporate liability lawyers will undoubtedly look to hold businesses negligent — and even C-Suite leaders personally liable — for failing to implement adequate safety- and security-related controls.
The responsibility then lies upon CISOs and CIOs to take the initiative to guide their boards and leadership teams on how to best ensure their organization is prepared to mitigate these security risks, rapidly detect and respond to ransomware and other intrusions and have controls in place to fully support the business need for digitization, without sacrificing security.
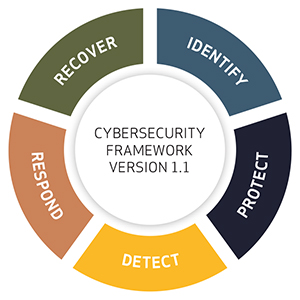
Source: NIST Cybersecurity Framework (CSF) v1.1
Keep reading for tips on how to effectively present IoT/OT security risk to the board:
- Educate the Board on the Changing Risk Landscape: Educating the board about how IT/OT convergence changes the threat landscape is the most crucial place to start. Rather than delving into bits and bytes, use anecdotes of real-world attacks on industrial control systems to highlight financial and corporate liability risks, such as the TRITON attack on safety systems in a petrochemical facility, the Ukrainian grid attacks, NotPetya – which shut down production facilities worldwide — and the Norsk Hydro ransomware attacks. And don’t be deterred by objections like “Why would nation-state attackers come after us?” The cyberattack tools and techniques used today by sophisticated nation-state adversaries quickly become available tomorrow to cybercriminal organizations and less sophisticated nation-states.
- Align with the Business: Make sure you spend time with your colleagues on the management team — before the board meeting — to ensure they understand how you’re aligned and supporting them in achieving their business objectives around digitalization, while at the same time minimizing risk and addressing regulatory compliance.
- Adopt a Cybersecurity Risk Management Framework: In 2014, the Cybersecurity Enhancement Act updated the role of the National Institute of Standards and Technology (NIST)1 to include identifying and developing cybersecurity risk frameworks for voluntary use by critical infrastructure owners and operators. A product of this, the NIST Cybersecurity Framework (CFS) was created to help organizations present a practical standard for operationalizing security controls based on their own business objectives. In other words, it’s an ideal tool as it presents a physical “plan” for board members to understand, track and set metrics that establish accountability, responsibility and authority over security networks. Different frameworks exist to tailor to specific industries, and the latest NIST report describes how IoT/OT-aware behavioral anomaly detection (BAD) reduces the risk of destructive cyberattacks for industrial organizations.
- Don’t Forget People & Process: Cybersecurity is everyone’s job, and technology is definitely not a silver bullet. Make sure you also have comprehensive security awareness programs in place to educate OT personnel about common risks such as plugging their laptops into control networks, sharing remote access credentials with third-party contractors and enabling direct internet access to IoT devices in control networks. “Trust but verify” by continuously monitoring your environment to ensure employees and contractors are adhering to published policies since even the best policies are ineffective if controls aren’t in place to make sure they’re being followed.
- Plot Your Path on a Maturity Model (It’s a Journey): Today's adversaries, ranging from nation-states to cybercriminals and hacktivists, are motivated, determined and highly capable of causing disruption and destruction. The goal of any security program is not to prevent all intrusions since a determined adversary will eventually penetrate your defenses, but rather to reduce the probability of an attack that will have a material impact on your firm. Show the board how you have a timetable to deploy effective controls to quickly spot attackers and kick them out before they shut down the plant, cause a safety or environmental incident, or steal sensitive intellectual property. Explain how you’re implementing network segmentation and zero-trust strategies to make it more difficult for attackers to pivot from initial footholds to higher-value assets and data. Unify IT and OT security monitoring and governance using common workflows and tools (SIEM, SOAR, etc.). Discuss how you’re using third-party audits, penetration testing, and Red Team exercises to regularly test your cyber resiliency. Use maturity models to illustrate how you’re progressing over time and continuously improving.
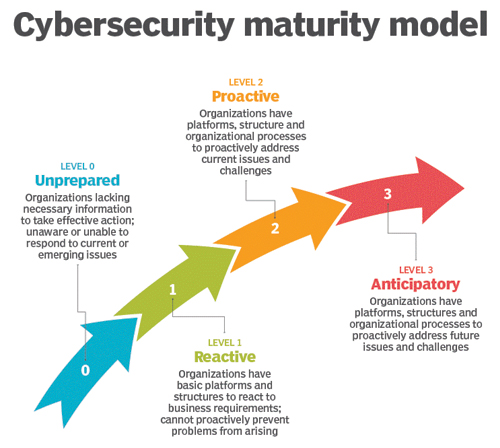
Source: Nemertes Research, 2018;
Illustration: Talex / Adobe Stock
In summary, IoT/OT security is all about protecting your people, production and profits. By aligning with the business, explaining your strategy in non-technical terms and helping boards understand that cyber risks are actually business risks (rather than “IT issues”), you have a much better chance of getting the leadership buy-in — and budgets — required to execute an effective IoT/OT security program.
 Phil Neray is VP of IoT & Industrial Cybersecurity for CyberX, a Boston-based security firm, which was recently acquired by Microsoft. Prior to CyberX, Neray held executive roles at IBM Security/Q1 Labs, Symantec, Veracode, and Guardium. Neray began his career as a Schlumberger engineer on oil rigs in South America and as an engineer with Hydro-Quebec. He has a BSEE from McGill University, is certified in cloud security (CCSK), and has a 1st Degree Black Belt in American Jiu-Jitsu.
Phil Neray is VP of IoT & Industrial Cybersecurity for CyberX, a Boston-based security firm, which was recently acquired by Microsoft. Prior to CyberX, Neray held executive roles at IBM Security/Q1 Labs, Symantec, Veracode, and Guardium. Neray began his career as a Schlumberger engineer on oil rigs in South America and as an engineer with Hydro-Quebec. He has a BSEE from McGill University, is certified in cloud security (CCSK), and has a 1st Degree Black Belt in American Jiu-Jitsu.
Reference:
1 National Institute of Standards and Technology (NIST) Cybersecurity Framework https://www.nist.gov/cyberframework







