Like many systems of systems, the electric grid is facing challenges as devices and applications originally intended to be either standalone or locally networked are now
being connected to the Internet. Additionally, the electric grid faces challenges as the need to reduce carbon output is resulting in rapidly increasing numbers of non-centralized renewable energy systems. Many renewable energy systems such as solar Photovoltaic (solar PV) are owned not by electric utilities but by customers, thus requiring new cyber controls to protect information flowing to and from the electric utility on utility-owned, private, and public communication networks. Other unique electric grid cyber challenges include the need to meet the North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) requirements and a business model being contested by non-profits such as the San Diego Community Choice Alliance. In the state of Illinois, more than two-thirds of residents’ energy is supplied by community choice aggregators (CCAs).
Electric grid cyber challenges can be met using systems engineering techniques including:
- Cyber Enterprise Architecture.
- Effective implementation of NERC CIP requirements.
- Consistent cybersecurity requirements for system procurement Requests for Proposals (RFPs).
- Cyber assessment for OT systems defining risks based on impacts to safety, reliability, key functions, processes and compliance.
Motivation for cyberattacks specifically targeting the electric grid ranges from individual hacktivists with an ax to grind to powerful nation-states that use attacks against their enemies. Threat motivations include theft of intellectual property, economic gain from stealing and then selling information, and the desire to create a high impact event such as the loss of electric power over an extended area – an event that is virtually guaranteed to generate wide-spread media attention which is the goal of many terrorist attacks.
It’s important to note that although the goal of most typical industrial and personal cyberattacks is economic gain – the goal of the most serious attacks is to cause widespread outages. The threat by nation-states against American utilities is not merely theoretical. As reported by the Department of Homeland Security (DHS), Russia has successfully attacked and gained access to power plant control rooms. Specifically, DHS stated that Russia has attempted to attack targets in the energy sector since 2016. In 2017 and 2018, the U.S. formally sanctioned Russia for their attempted cybersecurity attacks, including attacks against nuclear power plants. Further, Russia has demonstrated that they are more than willing to use cyberattacks against their enemies to cause grid outages as they have repeatedly done against Ukraine from 2015 onward.
Why do nation-states seek to use cyberattacks against their military and political enemies? The short answer is because cyberattacks are less costly than using more traditional military options. In the second half of the twentieth century, the U.S. and Soviet Union reached numerous nuclear disarmament treaties, followed by the breakup of the USSR and the subsequent creation of the Russian Federation. As Russia and other countries realized they could not successfully compete militarily, nations began what is known as asymmetrical warfare programs including cyberattacks.
Asymmetrical warfare allows nations to devote fewer resources against their targets than required by traditional military efforts. The advantages of being able to launch low-cost attacks against targets anywhere in the world through the Internet has proven to be a strategy used by many nations including Russia, North Korea, Iran and China. Further, in the case of cyberattacks against the electric grid, attacks are launched from the safety and convenience of offices in attackers’ home countries. To be fair, the U.S. also has what is euphemistically called offensive cyber operations in its arsenal.
Electric grids are a particularly attractive target for nation-states, terrorists and hackers, as electric power is critical for all aspects of modern life. Businesses, residences and government facilities all require power to operate; usually protecting only the most critical devices and systems with back-up power. For example, very few homes have backup generators, and many businesses have backup power only for safety-related equipment such as lights guiding people to emergency exits. Without power, most businesses and government offices are forced to close, resulting in outages causing significant economic losses.
All industries are at risk for cyberattacks, and the electric grid has many potential targets with more than 3,300 electric utility companies in the U.S., alone. Risks for electric grid organizations include both general and specific threats such as:
- Under-staffed security and operational departments.
- Inadequate policies, procedures and culture governing security.
- Inadequately designed systems and communication networks lacking defense-in-depth
- Large numbers of older communicating SCADA devices lacking cyber protection.
- Inadequately secured wireless communications.
- Non-dedicated communication channels.
- Remote access without appropriate access control, including remote vendor and subcontractor access.
- System administration mechanisms and software not adequately scrutinized, monitored or maintained.
- Insufficient use of tools to detect and report suspicious activities.
- Unauthorized or inappropriate applications/devices on networks.
- Control systems data typically not authenticated.
- Inadequately managed, designed or implemented critical support infrastructure.
- Maintenance procedures requiring manual installation of software/firmware updates that are installed with potentially compromised portable media, e.g., USB sticks.
Many cyberattacks on electric utilities have an end game. Cyberattacks typically begin with intentional, prolonged system probing and data gathering activities against specific targets with specified intent. Advanced Persistent Threats (APT’s) include unauthorized stealth reconnaissance, data gathering and vulnerability analysis of infrastructure, assets, networks, SCADA systems, data, and personal information. The intelligence data gathered is then used to develop more pervasive methods and to map out the infrastructure; i.e., dig deeper and harvest greater amounts of intelligence. At some point, the intelligence is leveraged to understand better how the target utility operates, thus enabling the attacker to launch clear, specific and focused attacks, usually with malicious intent. Most attacks are to gain information and data; not to shut down the grid. However, as noted previously, the most serious attacks do intend to cause power outages and if possible, extend these outages by causing physical damage to power grid devices which are not easily repaired or replaced such as generators or transformers.
A further complication for electric utilities is that their business systems and grid management operations require different cyber protection solutions. Utility IT and OT cyber protection needs are vastly different. Typically, cybersecurity protections for a utility’s business applications are similar to other businesses’ cyber protection methods. For example, business systems must provide protection for vast numbers of emails. Some emails contain malware for customer-facing web pages, linking to harmful content. Online payment systems must protect against theft of personal and credit card information. OT systems must protect against specialized SCADA attacks, such as the infamous Stuxnet attack, which targeted Siemens software and Programable Logic Controllers (PLCs).
Further, utility systems, such as Outage Management Systems (OMSs), must protect against both IT and OT threats. Depending on specific features, OMSs may be subject to multiple types of attacks. For example, utilities offering web pages for customers to report outages are subject to malicious content and malware from compromised web sites. Utilities’ customer service applications processing outages via phone are subject to business application attacks, and AMI-reported outages are subject to attacks on widespread mesh communications networks. Field crews and operational control centers, attempting to correct outages, face attacks against their SCADA and hand-held devices. Utilities need cybersecurity experts familiar with business and operational threats, vulnerabilities and protection, but instead, they often lack the funding and staff to hire and train the necessary IT and OT cyber experts.
Another substantial risk for utilities and their electric grids is attacks against subcontractors and vendors rather than against the utility itself. As the Wall Street Journal reported in January of this year, Russia successfully installed attacks on computers in small companies that provide services to utilities. Using techniques such as installing malware in utility industry online publications and by sending fake resumes with infected attachments, the attackers were able to penetrate control systems. Perhaps most troubling was the WSJ's report that the attacks appeared to be targeting companies that provide backup power systems, thus raising the possibility that attackers are confident in their ability to cause outages on the main grid and are now attempting to disrupt backup power systems as well.
A recent increasingly worrisome issue is exposure of OT systems including Advanced Distribution Management Systems (ADMS) to the Internet. Utilities want more data from customer-owned systems such as smart inverters, smart thermostats and electric vehicles to become inputs to the ADMS. Access to customer device data is typically provided over the Internet. Therefore, many operational control systems which were previously protected via air-gapping are now, or soon will be, exposed to cyber threats. Similar to personal computers in the 1980s, that were not designed with the Internet in mind, many SCADA control systems were not designed to prevent attacks from the Internet. As with earlier PCs, injection of malware onto SCADA systems is not difficult, as the systems simply were not designed to prevent Internet attacks. Just as two-way power flow caused by DERs requires different protection schemes, two-way communications to DERs and field devices require different cyber protection methods.
Another concern for utilities is that the effect of a successful attack can be worse than an outage. If an attack can render many devices unusable and insufficient spares exist, then the effect of the attack can persist longer and can be more serious than an actual outage. For example, if an attack can be delivered to 10 percent of solar PV inverters – than a successful attack may force all solar PV systems to be powered down. The complication for a utility is that determining which inverters are infected requires a time-consuming check of each inverter. Note, that in order to protect against a re-occurrence of the attack, an effective method of preventing further occurrences of installation of malware is also required – perhaps requiring a costly and time-consuming update of the inverters’ firmware and coordination with the inverter owners to implement any needed patches. Although this example describes an attack on solar inverters, a successful attack could be launched on devices ranging from substation transformers, down to the power electronics inside modern smart meters.
To prevent cyberattacks from disabling the grid, and to stop economic attacks, it is necessary to understand the steps of an attack. An attack typically involves many separate actions – and usually uses many pieces of malware. The steps of an attack, often referred to as an “anatomy of an attack,” include several iterations of the following activities:
- Observation: Research and analysis of potential sites to attack.
- Attack Identification: Selecting malware to use in the attack.
- Delivery: Physically sending cyberattacks to the targets.
- Installation: For successful attacks, the placing of malware on the target’s computers.
- Exploitation: Using information or access gained to the benefit of the attacker.
- Control: Using installed malware to interfere with a utility’s operations or business functions. Successful control actions include gaining access to T&D operator consoles.
In terms of addressing cybersecurity threats, System engineering offers several methods to help address the very real cyber threats to utility operations. Systems engineering activities most applicable to major cyber assessments are highlighted in blue in the Cyber SE Activities Table.
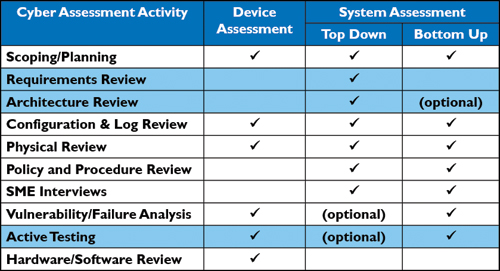
Cyber SE Activities Table
Systems engineering solutions for requirements reviews, architecture reviews and active testing include
Document and map cyber requirements to solutions.
- Map implementation of NERC CIP cybersecurity requirements to the specific plans, procedures, systems, people and location of artifacts demonstrating compliance known as “measures” in NERC CIP terminology. Use hyperlinks in a single document to each item to enable easy access to all implementation details for each requirement.
- Use a consistent set of cybersecurity requirements in all RFPs. Attackers will identify the weakest link during their Observation phase. It’s important to ensure all systems, especially vendor, subcontractor and field crew systems, are protected.
- Develop cybersecurity use cases describing how attackers will operate in each step of an attack. In each use case, be sure to include the specific requirements that will be used to attempt to block the attackers from progressing to the next attack step.
- Develop Cybersecurity Enterprise Architecture.
- Document an architecture cyber view dividing the utility systems into security zones and showing which cyber solutions are needed in each security zone. Include a security zone and cyber solutions for customer systems such as smart inverters, customer DERs, electric vehicles, smart meters and smart thermostats.
- Recognize IT and OT cyber systems face different threats and need different cybersecurity solutions starting with different cyber strategies and cyber architectures.
- Use industrial control system architectures as a starting point for utility OT cyber architecture.
- Coordinate IT and OT cyber architectures into an integrated enterprise architecture while ensuring both IT and OT cybersecurity experts have inputs to prevent unintended gaps in cyber protection.
- Review cyber architecture to verify establishment of security perimeters, placement of access points, information flows, dependencies and resiliency.
- Conduct integrated vulnerability/threat/failure analyses.
- Leverage requirements, enterprise architecture and testing artifacts in cyber assessments and analyses. For example, use the cyber architecture to identify potential injection sites for attacks and include requirements to prevent such attacks in the cyber use cases and procurement RFPs.
- Actively test cybersecurity with penetration tests. Do not stop testing after just a few cyber vulnerabilities are detected, but instead, attempt to locate each cyber vulnerability during each penetration testing cycle.
- Apply applicable techniques to IT and OT analyses. Techniques applicable to both IT and OT include vulnerability assessments, risk assessments, threat assessments, white/grey/black-box testing, penetration testing and auditing. Assessment most applicable to IT systems include HIPAA for healthcare and HR systems, Sarbanes Oxley (SoX) for financial systems and Payment Card Industry (PCI) for credit/debit card processing systems. NERC CIP is, of course, specifically targeted for energy sector OT and SCADA systems.
The primary objective of a cyber assessment is to identify risks. Traditional IT assessment methodologies typically utilize a concept of calculating risk (Risk=Impact x Probability/Cost). The traditional approach, however, is problematic when applied to the power grid or other OT domains as probability and costs are subjective numbers, and the resulting calculated risk is not universally understood. An alternative systems engineering technique for OT systems is to define risk in terms of the impact to areas such as safety, reliability, key functions, processes and compliance. The Risk Assessment Table combines safety, operational and NERC CIP compliance impacts into a sample risk assessment ranking methodology, using impact levels of critical, high, medium and low.
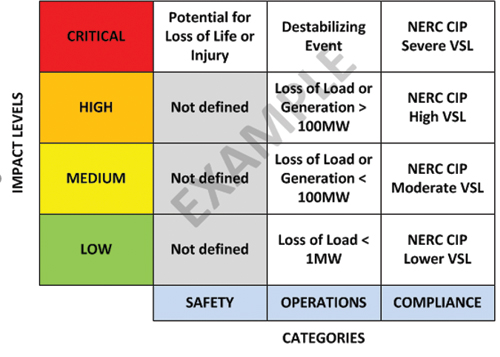
Risk Assessment Table
NREL has developed a 10-step Systems Engineering Approach, which can be accessed from their website at https://www.nrel.gov/esif/cybersecurity-resilience-10-step.html. Different Systems engineering methodologies use slightly different lists of cyber protection activities, but most are similar to NREL’s set of five which are
- Identify.
- Protect.
- Monitor.
- Respond.
- Recover.
One effective systems engineering technique is to verify that protection methods are in place for each activity; e.g., to verify that there are methods to identify, protect, monitor, respond to and recover from each identified threat. Additional protection methods can and should be added for identified gaps.
In summary, systems engineering techniques can help protect the electric grid from many cybersecurity challenges, including exposure of OT systems to Internet attacks, the growing numbers of customer-owned systems, and threats from nation-states, hackers and terrorists.

Director of Implementation Services for Enernex Kay Stefferud is a TOGAF® 9 certified enterprise architect with more than 35 years of experience in systems engineering, cybersecurity, architecture, program management, product development, renewable energy projects, commercial communications devices, software applications, real-time sensor systems, situational awareness and advanced energy resilient systems.







