Electric power companies increasingly are the targets of sophisticated attacks. These assaults include not just advanced cyber security threats, but physical attacks as well. At the same time, the quantity and types of communication and automation systems deployed by utilities continues to grow, increasing the utilities’ attack ‘surface.’ For a well-resourced attacker, the question often is not ‘if’ but ‘when’ it will compromise an organization, and advanced attacks have been known to escape detection for weeks or months.
As this threat landscape has intensified, there is a greater need for a coordinated view of all aspects of an organization’s security posture, including how events may impact that posture and how best to respond to those events. Utilities have greatly increased their security monitoring and defenses in the last several years, deploying defense-in-depth strategies, real-time alerting, and security awareness training. However, companies that only react to events spend most of their energy putting out fires, struggling to keep up with the current threats.
An intelligence-driven approach to cyber defense, using threat indicators, gets ahead of attackers while quickly responding to incidents as they occur. Unfortunately, the security monitoring necessary to execute this approach typically happens in different parts of organizations. These security operations centers (SOCs) are common in physical security, business, and industrial control environments. Many utilities have one or more of these individual SOCs responsible for defined physical regions or business functions.
Utilities increasingly see security benefits in integrating these information silos, and EPRI is working with companies and vendors on technologies and applications for creating integrated security operations centers, or ISOCs. An ISOC brings together the many isolated security monitoring and response functions into a unified framework. The benefits include:
- Real-time intelligence
- Improved analyses of vulnerabilities and threats across organizational domains
- Efficient forensics and root cause analyses
- Unified (corporate information technology (IT) and operations technology [OT]) security incident management
- Centralized configuration and patch management
- Optimization of security resources
- Building workforce trust relationships across business functions
Figure 1 shows a potential architecture for an ISOC, which can aggregate and correlate security logs and events from IT systems, OT systems, security appliances, and physical security systems. If a utility has a network operations center (NOC) for its field networks, events from the NOC or other network management systems can be integrated as well. While these sources help a utility identify and react to security incidents across its enterprise, they are not sufficient to support advanced threat management. This requires an ISOC also receives input from external threat and vulnerability sources, providing analysts with the information necessary to prevent threats from becoming incidents.
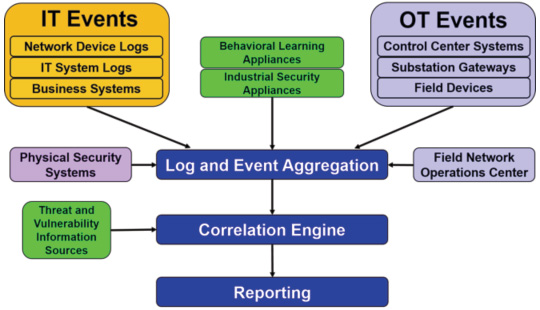
Figure 1: Example ISOC Architecture
An advanced ISOC could integrate several other information sources as well, such as a work management system and power operations data from the SCADA system. Having more information available to the correlation engine and security analysts can provide more indicators of attack and potentially reduce false positives. Below are several examples of scenarios which an ISOC could help to detect more efficiently:
- Anomalous power system behavior is logged by the ISOC from a device or system at a substation. The ISOC also logged a physical security event at the same substation shortly before the anomalous SCADA behavior was detected. The appropriate SCADA operator could be informed of the possible correlation of events, allowing them to respond appropriately.
- An IT employee logs in remotely to perform maintenance on the Historian database. The ISOC detects that no work order exists in the work management system for this work to be performed. The remote connection to the database could then be terminated.
- An employee has logged into a workstation in the control center. However, the physical access control system badge credentials to access the control center do not match the login credentials from the identity management system. An onsite facilities security team could be dispatched to investigate.
- The IT operations center is alerted to a USB drive plugged in to a field device at the substation. The physical security monitoring center is alerted of a cut fence and an unauthorized person on the grounds of a substation. A security team could be dispatched to the substation to investigate.
Migrating from technology or business unit SOCs to an enterprise ISOC can be a multi-year, phased process that requires significant planning and investment. Several internal stakeholders must be engaged to reach consensus on the business drivers, potential challenges, and high-level phases of the effort. In 2013, EPRI published Guidelines for Planning an Integrated Security Operations Center (http://www.epri.com/abstracts/Pages/ProductAbstract.aspx?ProductId=000000003002000374). This technical update, which can be downloaded at no cost by searching for the report number on EPRI’s website, focuses on the initial steps of setting up an ISOC – developing the business case, identifying potential organizational challenges, determining tradeoffs for different ISOC architectures, and planning the implementation process.
EPRI’s research for 2014 focuses on the process of integrating the physical and cyber security monitoring of control center systems into an ISOC – understanding potential security failure scenarios, developing requirements, understanding the impact of different ISOC architectures on the security monitoring process, and establishing guidelines for the implementation process.
EPRI’s Cyber Security Research Lab (CSRL) in Knoxville, Tennessee directly supports the ISOC research. The CSRL is generally used to conduct proof-of-concept and use-case testing to support EPRI’s annual research, as well as focused testing for utility projects. Currently, ISOC research is being conducted in the CSRL through testing of various attack scenarios with an array of vendor products and devices. Vendor solutions that make up the ISOC test bed include:
- Security Incident and Event Management (SIEM) software
- Protocol-aware firewalls
- Security gateways
- Security appliances
- Substation SCADA devices
- Security cameras
- Video management software
- Logical and physical access control systems
- Ballistic detection simulation software

Figure 2: ISOC Data Sources
As the security threats to utilities become more sophisticated, companies must leverage their security monitoring resources more efficiently and intelligently to stay ahead of the attackers. A centralized approach for threat management provides greater situational awareness of security events and threats across the entire enterprise, improving threat analyses, optimizing security resources, and supporting better root-cause analyses.
About the Author
 Ralph King is a Principal Technical Leader for Cyber Security in the Power Delivery and Utilization (PDU) Sector at the Electric Power Research Institute (EPRI). Prior to joining EPRI, he spent over thirty-years in the electric power industry where he served in various leadership roles in security and information technology. His academic background is in Computer Science, Mathematics, and Business.
Ralph King is a Principal Technical Leader for Cyber Security in the Power Delivery and Utilization (PDU) Sector at the Electric Power Research Institute (EPRI). Prior to joining EPRI, he spent over thirty-years in the electric power industry where he served in various leadership roles in security and information technology. His academic background is in Computer Science, Mathematics, and Business.






